Many successful hackers go out of their way to separate their real names from their hacker handles. But among some old-school Russian hackers it’s rare to find big players who have done little to prevent people from knowing who they are in real life. A case study in this case is “x999xx,” a pseudonym chosen by a respected Russian hacker who provides initial network access to various ransomware groups.
x999xx is a well-known “access broker” who often sells access to hacked corporate networks – often in the form of remote access credentials – and compromised databases containing large amounts of personal and financial data.
In an analysis published in February 2019, the cyber intelligence company Flashpoint called x999xx one of the most senior and effective members of a high-level Russian-language cybercrime forum. Exploitationwhere x999xx can often be seen advertising the sale of stolen information and network credentials.
In August 2023, x999xx sold access to a company that develops software for the real estate industry. In July 2023, x999xx advertised the sale of Social Security numbers, names, and dates of birth for citizens of every state in the US (anonymized in the auction).
A month earlier, x999xx posted a series of 80 details taken from a major Australian retail company. “You can use this data to search for ransom or do something different with it,” wrote x999xx on Exploit. “Unfortunately, the mistake was quickly cleared. [+] no one has used the data yet [+] data has not been used to send spam [+] data is waiting for its time.”
In October 2022, x999xx sold management access to a US healthcare provider.
ALIAS: MAXNM
An old account with the name x999xx appeared in 2009 on a Russian-language cybercrime forum It is confirmedunder email address [email protected]. Ozersk is a city in Chelyabinsk Oblast in west-central Russia.
According to the breach tracking service Constella Intelligence, the address [email protected] was used more than a decade ago to create an account on Vktontakte (Russian answer to Facebook) under the name Maxim Kirtsov from Ozersk. The profile of Mr. Kirtsov – “max” — says his birthday is September 5, 1991.

Personal photos Maxnm shared on Vktontakte in 2016. Caption machine translated from Russian.
User x999xx registered in the Russian-language cybercrime community Evil 2014 using an email address [email protected]. Constella says this email address was used in 2022 by a Russian forwarding service cdek.ru by a Maksim Georgievich Kirtsov from Ozersk.
A further search of these contacts reveals that prior to 2009, x999xx used the handle Maxnm on Russian cybercrime sites. Cyber intelligence company Intel 471 finds a user Maxnm registered in Zloy in 2006 at an Internet address in Chelyabinsk, using an email address. [email protected].
That email address was used to create Maxnm accounts on several other criminal platforms, including Spamdot again Exploitation in 2005 (also from Chelyabinsk), and Damagelab in 2006.
Search on Constella for the Russian translation of Kirtsov’s full name – Кирцов Максим Георгиевич – Brings multiple accounts registered to it [email protected].
Review of the digital footprint of [email protected] at industries reveals that this address was used ten years ago to register an account that is still active imageshack.com under the name x999xx. That account has many screenshots of financial statements from various banks, chat logs with other hackers, and even hacked websites.
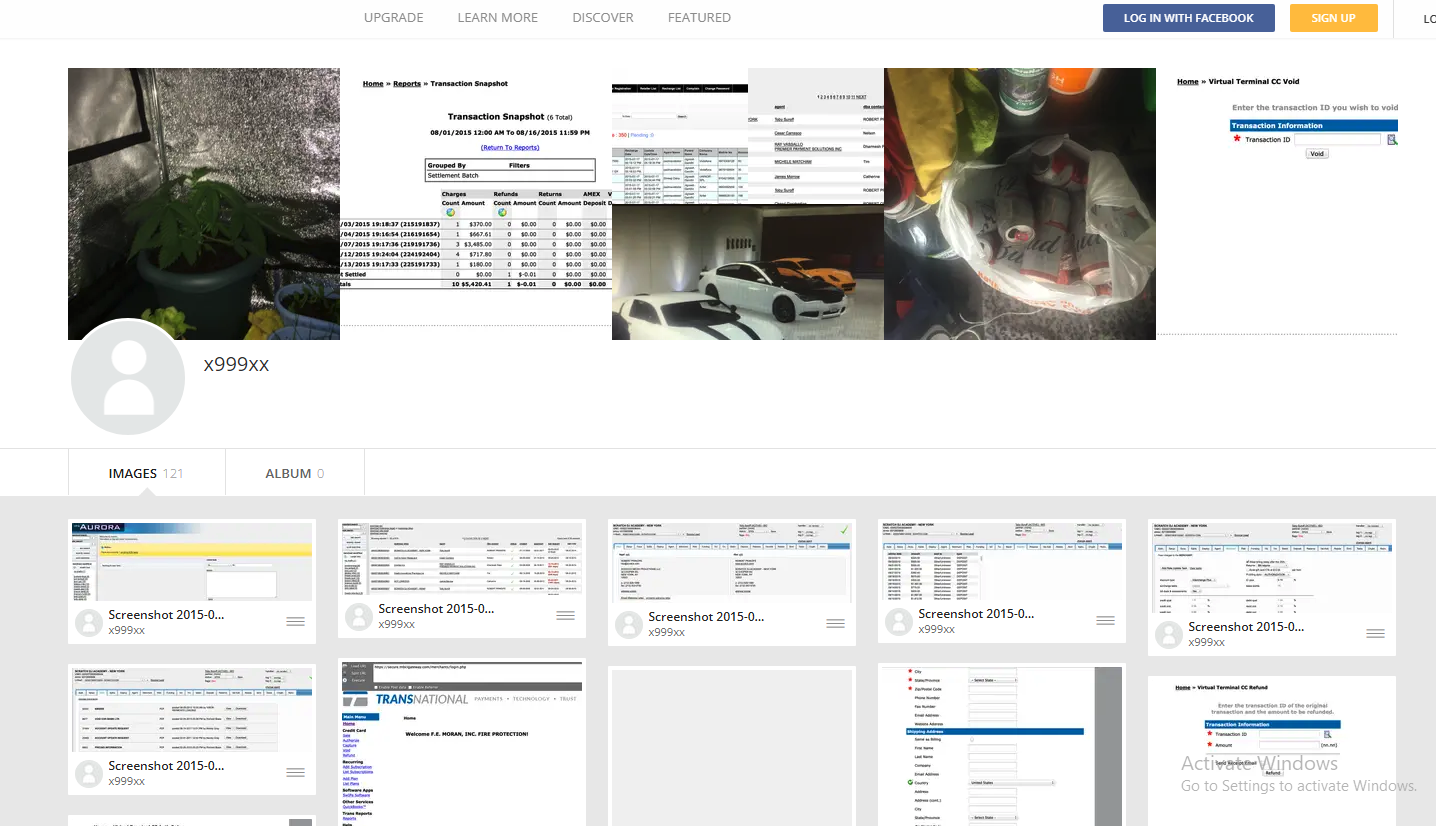
Imageshack’s x999xx account includes screenshots of bank account balances from multiple financial institutions, as well as chats with other hackers and photos of home weed.
Some of the images from that Imageshack account also appear on Kirtsov’s Vkontakte page, including pictures of cars he owns, as well as pictures of crushed marijuana plants. Kirtsov’s Vkontakte profile states that in 2012 he was a member of the Faculty of the Ozersk Technological Institute National Research Nuclear University.
The Vkontakte page lists Kirtsov’s work as a named website Ozersk[.]today, which appears to be a blog about life in Ozersk. However, in 2019 the security company Recorded Future published a blog post that found this domain was being used for malicious hosting Cobalt Strike the server.
Cobalt Strike is a commercial network penetration testing and detection tool sold only through vetted partners. But stolen or illegally obtained Cobalt Strike licenses are often abused by cybercriminal groups to help lay the groundwork for installing ransomware on a victim’s network.
In August 2023, x999xx sent a message to Exploit saying he was interested in buying a licensed version of Cobalt Strike. A month earlier, x999xx filed an Exploit complaint against another forum member named Cobaltforce, a former colleague who suddenly and for a long time disappeared from the public leaving x999xx and others exposed. Cobaltforce hired people with experience in using Cobalt Strike for ransomware operations, and offered to monetize access to hacked networks for a share of the profits.
DomainTools.com acquires ozersk[.]today is registered to the email address [email protected]which was also used to register about twenty-two other domains, incl x999xx[.]biz. Almost all those domains were registered to Maxim Kirtsov from Ozersk. Below is a mind map used to track what is said in this story.
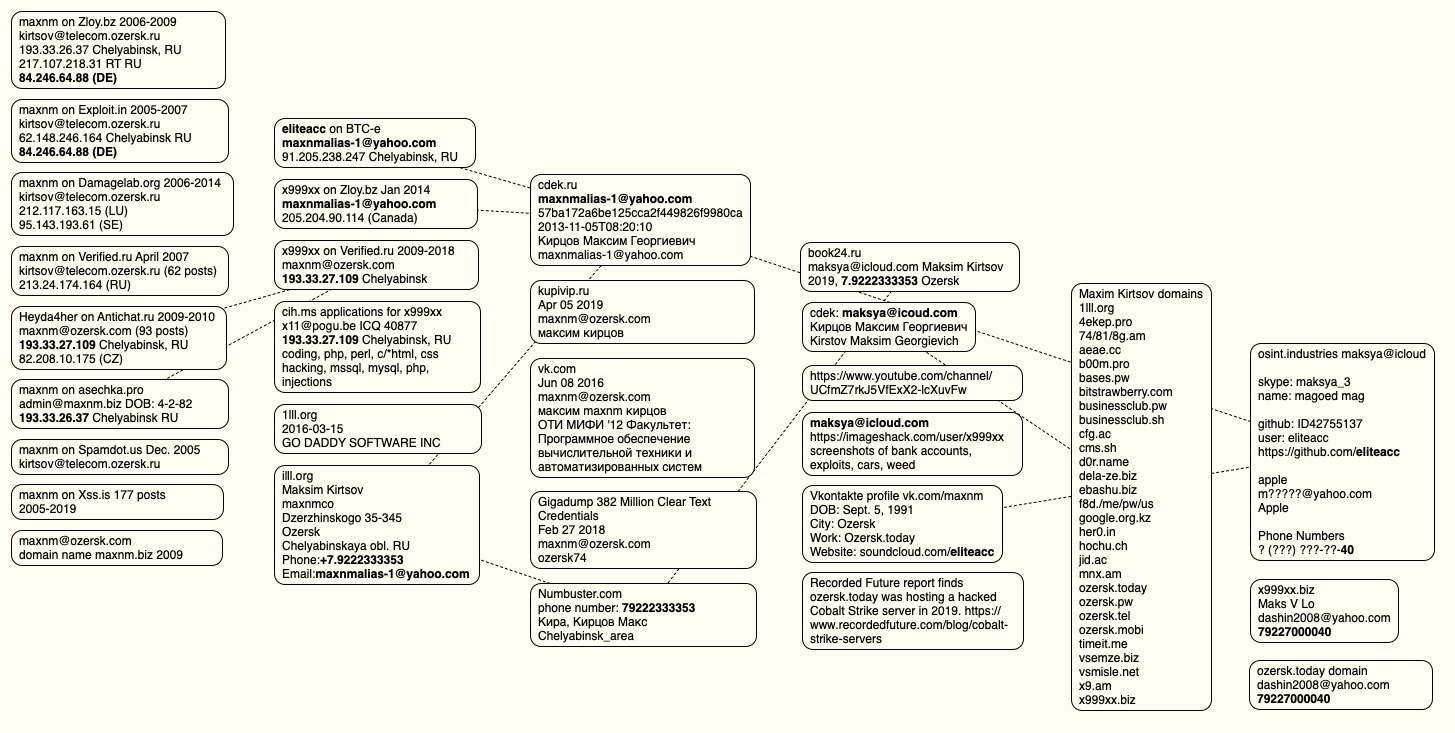
Visual representation of data points connecting x999xx to Max Kirtsov.
x999xx is the largest member of the Russian webmaster forum “Gofuckbiz,” with more than 2,000 posts in nearly a decade, according to Intel 471. In another post from 2016, x999xx asked if anyone knew where to buy a heat lamp which imitates sunlight. , explaining that one of the rabbits they raised had recently died due to lack of light and heat. Mr. Kirtsov’s Vkontakte page includes several photos of caged rabbits from 2015 and earlier.
GUARANTEE
Reached by email, Mr. Kirtsov admitted to being x999xx. Kirtsov said that he and his team are regular readers of KrebsOnSecurity.
“We are glad to hear and learn,” replied Kirtsov.
Asked if he was concerned about the legal and ethical implications of his work, Kirtsov downplayed his role in the ransomware, saying he was more focused on harvesting information.
“I consider myself to be as committed to morals as you are,” Kirtsov wrote. “I have also started research and now I am training students. You may have seen my posts on the forum, which I think you are aware of from information gathered from public sources, perhaps using the new tool you reviewed.”
“Regarding my post about selling access, I must honestly admit, when I review my actions, I remember such statements but I believe they did not happen,” he continued. “Many are using the forum to make a living, which explains why listings have dropped – they simply stop working.”
Kirtsov asserted that he is not interested in harming health institutions, only in stealing their information.
“Regarding health-related issues, I once got acquainted with rich webmasters who paid up to $50 for every 1000 emails with health topics,” says Kirtsov. Therefore, I was not interested in sensitive information from medical facilities such as X rays, insurance numbers, even names; I only focus on emails. I am proficient in SQL, hence I am comfortable handling data such as IDs and emails. And I’ve never done spam or anything like that.”
At Russian crime forums, x999xx said he doesn’t understand anyone in Russia, and has little to fear from domestic law enforcement agencies as long as he stays focused on foreign enemies.
The x999xx way of not caring about personal security is the glasses of He stoppedanother top Russian access broker who sold access to countless organizations and even used their own ransomware programs.
“Don’t panic where you live, go here, and don’t go abroad,” said Wazawaka, speaking of his own song. “Mother Russia will help you. Love your country, and you will always do nothing.”
In January 2022, KrebsOnSecurity followed the clues left by Wazawaka to identify him as 32 years old. Mikhail Matveev from Khakassia, Russia. In May 2023, the US Department of Justice accused Matveev of being a key figure in several syndicated ransomware groups that took hundreds of millions of dollars from victims’ organizations. I US State Department is offering a $10 million reward for information leading to the capture and/or prosecution of Matveev.
Perhaps realizing that many top ransomware criminals are untouchable as long as they live in Russia, western law enforcement agencies have begun to focus more on getting into the heads of those people. These so-called “psyops” are aimed at installing ransomware-as-a-service operations, disrupting major cybercriminal services, and undermining trust between cybercriminal communities.
While the authorities in the US and the UK announced in February 2024 that they would go in and seize the infrastructure used by famous people. LockBit ransomware gang, they borrowed the existing design of LockBit’s victim-shaming website to link instead to press releases about the takedown, and installed a countdown timer that ended up being replaced by the identity of the alleged leader of LockBit.
In May 2024, law enforcement agencies in the United States and Europe announced Operation Endgame, a coordinated action against some of the most popular cybercrime platforms for delivering ransomware and data-stealing malware. The Operation Endgame website also featured a countdown timer, which served as a tease with the release of several animated videos simulating the same type of flashy, short commercials that cybercriminals often produce to promote their services online.
Source link