The ransomware team has been called The Dark Angels He made headlines last week when it emerged that the crime group had just received a record $75 million data payment from a Fortune 50 company. Security experts say the Dark Angels have been around since 2021, but the group doesn’t get much press because it operates alone and keeps a low profile, choosing one target at a time and chooses mass data theft over disrupting the victim’s operations.
Photo: Shutterstock.
Security firm Zscaler ThreatLabz this month ranked Dark Angels as the top ransomware threat of 2024, noting that in early 2024 a victim paid the ransomware group $75 million — the highest amount for any ransom payment previously recorded. ThreatLabz found that Dark Angels has carried out the largest ransomware attack to date, yet little is known about this group.
Brett Stone-Gross, senior director of threat intelligence at ThreatLabz, said the Dark Angels operate using a completely different playbook than most other ransomware groups. First, he said, Dark Angels does not use a ransomware-related model, which relies on hackers for hire to install malicious software that shuts down infected systems.
“They don’t really want to make headlines or cause business disruption,” Stone-Gross said. “They’re about making money and attracting as little attention as possible.”
Most of the ransomware groups maintain the victim’s leaked sites and threaten to publish the stolen data of the target unless a ransom demand is paid. But the Dark Angels did not have a place to insult the victims until April 2023. And the place of the leak is not well marked; it is called Dunghill Leak.
A place of shame for the victims of the Dark Angels, Dunhill Leak.
“There’s nothing glamorous about them,” Stone-Gross said. “For a long time they didn’t even want to make a big headline, but maybe they feel compelled to make that leak because they want to show that they are serious and that they will send the information of the victims and make it accessible. “
The Dark Angels are thought to be a Russian-based cybercriminal organization whose distinguishing feature is stealing truly staggering amounts from large companies in many sectors, including healthcare, finance, government and education. For large enterprises, the group released between 10-100 terabytes of data, which could take days or weeks to transfer, ThreatLabz found.
Like many ransomware groups, Dark Angels will publish stolen data from victims who don’t pay. Some of the more notable victims listed in the Dunghill Leak include a global food distribution firm Sysco, which disclosed a ransomware attack in May 2023; and the travel booking giant Saberwhich was beaten by Dark Angels in September 2023.
Stone-Gross said Dark Angels are often reluctant to use ransomware because such attacks work by shutting down the target’s IT infrastructure, often causing the victim’s business to grind to a halt for days, weeks or even months on end. And those kinds of breaches tend to make headlines quickly.
“They choose selectively whether they want to use ransomware or not,” he said. “If they see that they can encrypt some files that won’t cause a lot of disruption – but will give them a ton of data – that’s what they’ll do. But really, what sets them apart from the rest is the amount of data they steal. It’s a huge order of magnitude with the Dark Angels. Companies that lose a lot of data will pay these high ransoms. “
So who paid the record $75 million ransom? The Sleep Computer revealed on July 30 that the victim is a pharmaceutical giant Cencora (before Company AmeriSourceBergen Corporation), which reported a data security incident in US Securities and Exchange Commission (SEC) on February 21, 2024.
The SEC requires publicly traded companies to disclose a potential cybersecurity event within four days of the incident. Cencora is currently #10 on the Fortune 500 list, generating over $262 billion in revenue last year.
Cencora did not respond to questions about whether it made a ransom payment in connection with the February cybersecurity incident, and referred KrebsOnSecurity to the charges listed under “Other” in the restructuring section of its latest quarterly financial report (PDF). That report shows the company incurred more than $30 million in costs associated with the breach.
Cencora’s quarterly statement said the incident affected the legacy private information platform in one country and the ability of the foreign business unit to operate in that country for about two weeks.
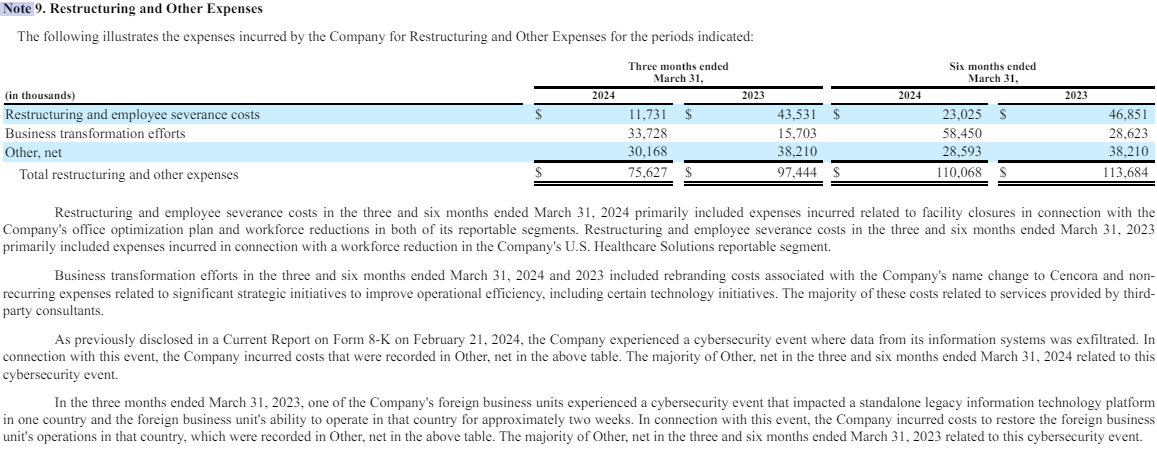
Cencora’s first quarter 2024 report documents a $30 million charge associated with a data release event in mid-February 2024.
In its latest State of Ransomware report (PDF), the security firm Sophos they found that the average payout for ransomware has increased fivefold in the past year, from $400,000 in 2023 to $2 million. Sophos said In more than four-fifths (82%) of the cases, the ransom funding comes from multiple sources. In total, 40% of the total ransom money came from the organizations themselves and 23% from the insurance providers.
Read more: threatLabz ransomware report (PDF).
Source link