Many GitHub users this week received a phishing email warning about critical security holes in their code. Those who clicked on the link for information were asked to disassociate themselves from the bots by pressing a combination of keyboard keys that trigger Microsoft Windows downloading password-stealing malware. Although it is unlikely that many programmers will fall for this scam, it is worth noting because the less targeted versions are likely to be more successful compared to the average Windows user.
A student named Chris shared an email he received this week that drove GitHub’s security team crazy and warned: “Hello! We have found a security vulnerability in your endpoint. Please contact us at https://github-scanner[.]com for more information on how to fix this issue.”
Visiting that link generates a web page that asks the visitor to “Verify You’re Human” by solving a strange CAPTCHA.
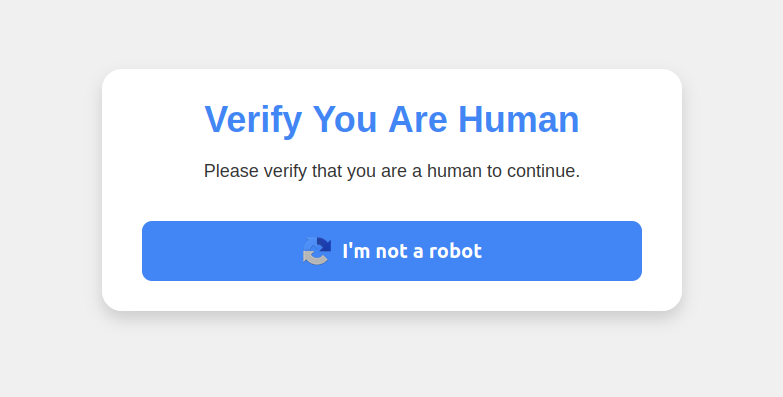
This malware attack masquerades as a CAPTCHA intended to distinguish humans from bots.
Clicking on the “I’m not a robot” button generates a pop-up message asking the user to take three consecutive steps to prove their identity. Step 1 consists of simultaneously pressing the keyboard key with the Windows icon and the letter “R,” which opens the Windows “Run” command that will run any specified program that is already installed on the system.
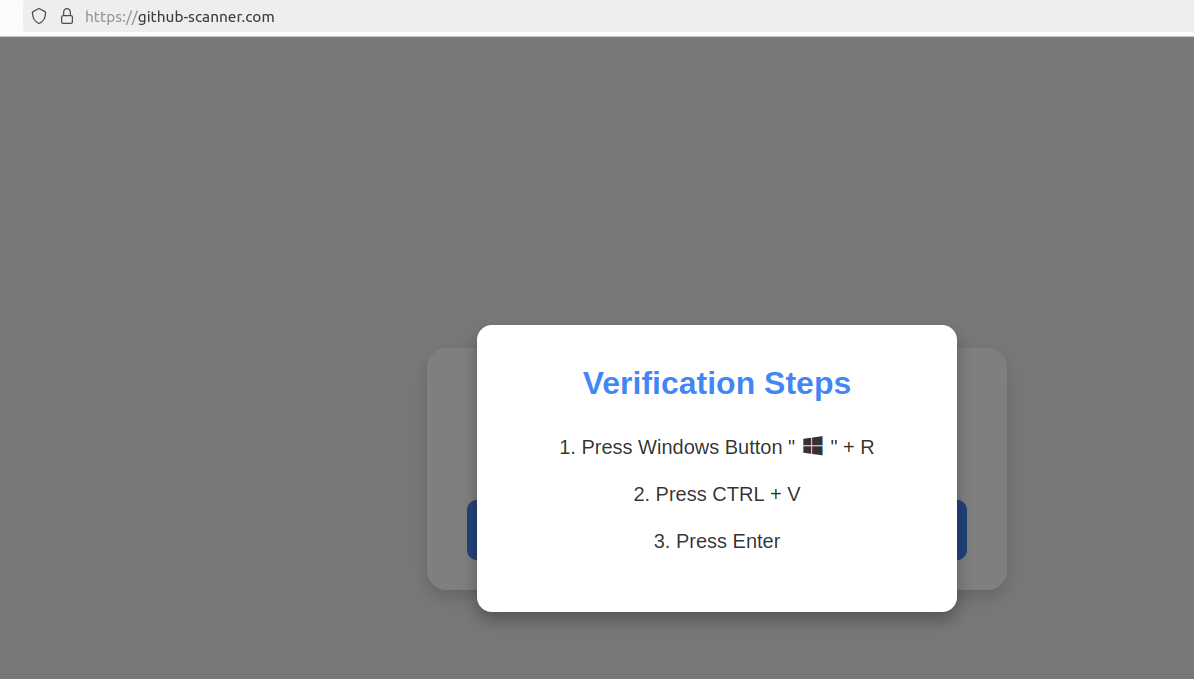
Using this series of keystrokes prompts the built-in Windows Powershell to download password-stealing malware.
Step 2 asks the user to press the “CTRL” key and the letter “V” at the same time, which pastes the malicious code into the site’s virtual clipboard.
Step 3 – pressing the “Enter” key – causes Windows to start PowerShell command, then download and execute the malicious file on github-scanner[.]com called “l6e.exe.”
PowerShell is a powerful, cross-platform automation tool built into Windows designed to make it easy for administrators to perform tasks on a PC or across multiple computers on the same network.
According to the analysis of the malware scanning service Virustotal.comThe malicious file downloaded by the attached script is called Lumma Stealerand is designed to find any credentials stored on the victim’s PC.
This phishing campaign may not have fooled many programmers, no doubt traditionalists understand that pressing the Windows keys and “R” will open the “Run” prompt, or that Ctrl-V will dump the contents of the clipboard.
But I bet the same method will work well to trick some of my tech-savvy friends and relatives into running malware on their PCs. I’d also bet that none of these people have ever heard of PowerShell, let alone had the chance to open a PowerShell terminal on purpose.
Given those facts, it would be nice if there was an easy way to disable or at least severely limit PowerShell to normal end users for whom it might be a huge liability.
However, Microsoft strongly advises against nixing PowerShell because some core system processes and functions may not function properly without it. In addition, doing so requires tinkering with sensitive settings in the Windows registry, which can be a daunting task even for the uninitiated.
Still, it wouldn’t hurt to share this article with the Windows users in your life who fit a less experienced profile. Because this scam has a lot of room to grow and create.
Source link