Federal authorities have arrested and charged a 20-year-old US Army soldier on suspicion of being Cyberphant0ma hacker who was selling and leaking sensitive customer phone records was stolen earlier this year AT&T again Verizon. As first reported by KrebsOnSecurity last month, the accused is a newly appointed communications specialist in South Korea.
One of several selfies on Cameron Wagenius’ Facebook page.
Cameron John Wagenius20, was arrested near the Army base at Fort Hood, Texas on Dec. 20, after being charged with two felony counts of illegally transferring confidential phone records.
The short, two-page indictment (PDF) does not name specific victims or the hacking activity, nor does it include any personal information about the defendant. But an interview with Wagenius’ mother — a Minnesota native Alicia Roen – fill in the blanks.
Roen said that before his son’s arrest, he admitted that he was related to him Connor Riley Mouckaaka”Jewish,” a large-scale hacker from Canada who was arrested in late October for stealing data from multiple companies that stored data in a cloud firm. Snowflake.
In an interview with KrebsOnSecurity, Judische said he was not interested in selling the data he had stolen from Snowflake’s customers and telecom providers, preferring to give it to Kiberphant0m and others. Meanwhile, Cyberphant0m said in Telegram posts that he was responsible for hacking at least 15 telecommunications firms, including AT&T and Verizon.
On November 26th, KrebsOnSecurity published an article following the trail of clues left by Cyberphantom indicating that he was a US Army soldier in South Korea.

18-year-old Cameron Wagenius, who is joining the US Army.
Ms Roen said Cameron had worked in radio signals and network communications at a military base in South Korea for the past two years, returning to the United States periodically. He said Cameron had always been good with computers, but he had no idea he might be involved in a robbery.
“I have never seen him rob,” said Roen. “It really shocked me when we found this.”
Ms Roen said Cameron joined the Army when it was just growing up, following in his older brother’s footsteps.
“He and his brother when they were 6 and 7 years old would ask for MREs from other countries,” he recalled, referring to the “ready-to-eat meals” issued by the military. “Both always wanted to be in the Army. I don’t know exactly where things went wrong.”
Soon after news of Moucka’s arrest broke, Cyberphant0m was posted to the hacker community. BreachForums what they said was AT&T phone calls The president-elect Donald J. Trump and for Vice President Kamala Harris.
“If you don’t reach us at @ATNT all government phone records will be leaked,” Kiberphant0m said, signing off their post with multiple “#FREEWAIFU” tags. “Don’t you think we don’t have plans in case we get arrested? Think again.”
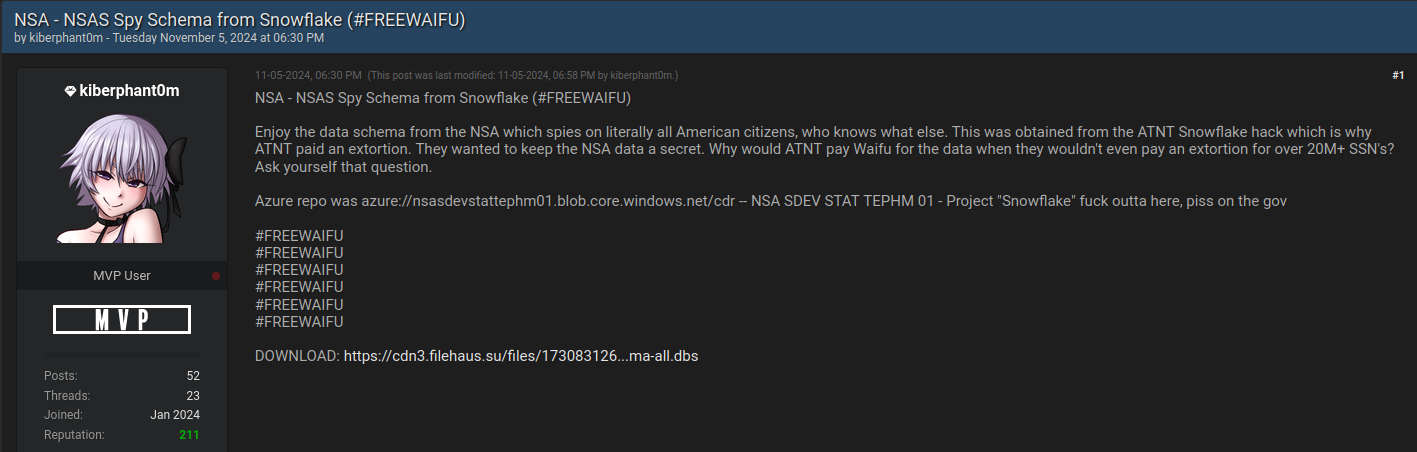
Cyberphant0m posting what he says is a “data schema” stolen from the NSA via AT&T.
That day, Kiberphant0m posted what they called a “data schema” from US National Security Agency.
On Nov. 5, Cyberphant0m provided records of stolen phone calls to Verizon’s push-to-talk (PTT) customers – mostly US government agencies and emergency first responders. On Nov. 9, Kiberphant0m posted a sales thread on BreachForums offering a “SIM swap” service targeting Verizon PTT customers. In SIM swapping, fraudsters use hacked or stolen information from mobile phone company employees to divert the target’s phone calls and text messages to a device they control.
The profile picture on Wagenius’ Facebook page was removed within hours of my Nov. 26 identifying Cyberphant0m as a possible US Army soldier. However, many of his profile pictures still exist, including several that show Wagenius in uniform while holding various Army-issued weapons.
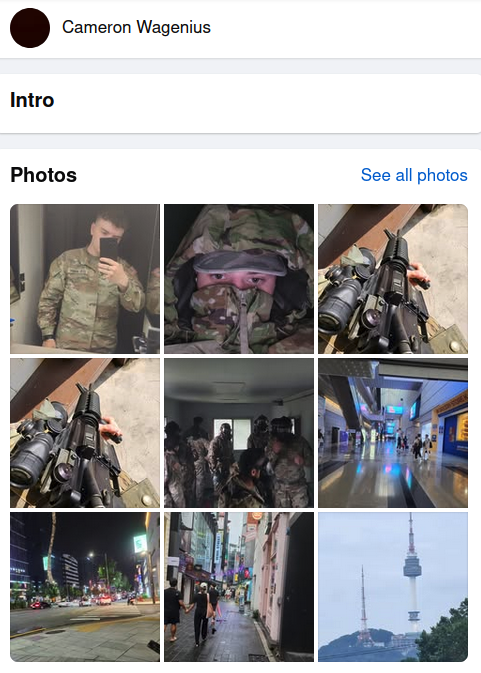
Several profile pictures appear on Cameron Wagenius’ Facebook page.
A November issue on Cyberphant0m cited his own Telegram messages saying he had a large botnet used for denial-of-service (DDoS) attacks to knock websites, users and networks offline. In 2023, Cyberphant0m sold remote access information for a major US defense contract.
Allison Nixon is a research officer at New York-based cybersecurity firm Unit 221B that is helping track down the identity of Cyberphant0m. Nixon was among the few security researchers who faced harassment and some threats of violence from Judische and his associates.
“Scamming the President and VP anonymously as a member of the military is a bad idea, but it’s an even worse idea to harass people who specialize in not exposing hackers,” Nixon told KrebsOnSecurity. He said investigations conducted at Cyberphant0m show that law enforcement is getting better and faster at going after cybercriminals – especially those living in the United States.
“Between us, and an anonymous colleague, we discover his opsc error on November 10 in his last Telegram job on December 6, law enforcement set a speed record for the fastest time to change an American cybersecurity case that I have seen in my work. ,” he said.
Nixon asked to share a message for all the other Cyberphant0ms out there who think they are missing and under arrest.
“I know that young people involved in Internet crime will read these articles,” said Nixon. “You need to stop acting stupid and get a lawyer. Law enforcement wants to put you in jail for a long time.”
The lawsuit against Wagenius was filed in Texas, but the case was transferred to the US District Court for the Western District of Washington in Seattle.
Source link