Citizens across the United States are inundated with text messages purporting to be from toll road drivers IE-ZPasswarns that recipients face fines if the crime toll remains unpaid. Researchers say the rise in SMS spam coincides with new features added to phishing kits sold in China that make it easier to set up deceptive decoys that trick toll road users in many US states.
Last week, i Massachusetts Department of Transportation (MassDOT) has warned residents to be aware of a new phishing or “phishing” scam targeting users EZDriveMAall of MassDOT’s electronic payment system. Those who fall for this scam are asked to provide payment card data, and will eventually be asked to provide a one-time password sent via SMS or a mobile authentication app.
Reports of similar phishing attacks on customers of other US government agencies emerged around the same time as MassDOT’s warning. Floridians have reported receiving serious SMS phishing attacks SunpassFlorida prepaid plan.
This phishing module for manipulating MassDOT’s EZDrive system was released on Jan. 10, 2025 by a Chinese phishing service called “Lighthouse.”
In Texas, residents say they have received messages about unpaid bills North Texas Toll Authority. Similar reports came from students in California, Colorado, Connecticut, Minnesota, and Washington. This is by no means an exhaustive list.
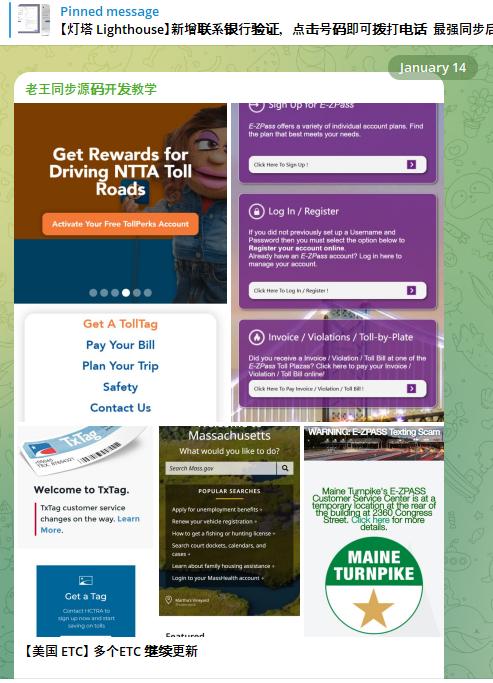
A new module from the Lighthouse SMS phishing kit released on Jan. 14 directed North Texas Toll Authority (NTTA) customers.
In each case, the emergence of these SMS phishing attacks has coincided with the release of new phishing kit capabilities that closely mimic these toll operator websites as they appear on mobile devices. Notably, no phishing pages will load even if the website detects that the visitor is coming from a mobile device.
Ford Merrill works in security research at SecAlliance, a CSIS Security Group company. Merrill said the number of SMS phishing attacks targeting road operators spiked after the New Year, when at least one Chinese cybercriminal group known to sell SMS phishing services began offering new phishing pages designed to trick state taxpayers. US variety.
According to Merrill, many China-based cybercriminals sell SMS-based phishing services each with hundreds or thousands of customers. The main goal of these services, he said, is to elicit enough information from victims that their payment cards can be placed in mobile wallets and used to purchase goods in physical stores, online, or to launder money through shell companies.
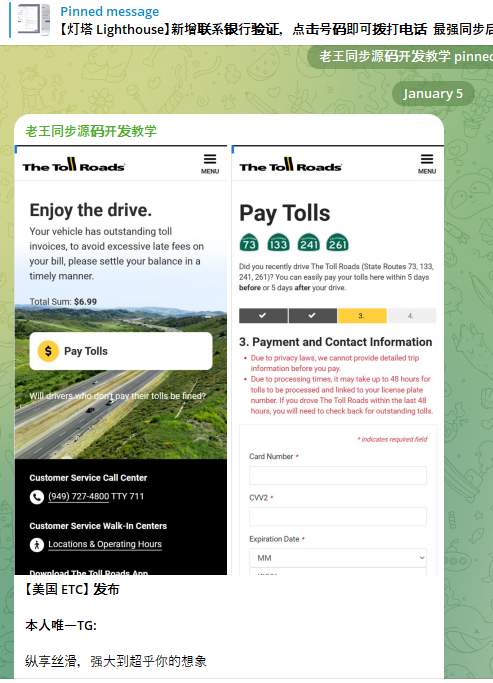
Part of China’s phishing kit is Lighthouse designed to target customers on The Toll Roads, which refers to several interstate highways that pass through Orange County, Calif.
Merrill said the various providers of these SMS phishing tools have often impersonated shipping companies, tax authorities, and even governments with tax refund scams and visa or immigration renewal scams targeting people who may be living abroad or recently arrived in the country.
“What we are seeing with these toll scams is the continuation of Chinese groups breaking packages from redelivery systems to toll roads,” said Merrill. “Everyone right now is sick and tired of getting these package attacks, so now it’s a new twist on the scam.”
In October 2023, KrebsOnSecurity wrote about a significant increase in phishing scams targeting SMS. US Postal Service customers. That story revealed that this operation was related to the innovations introduced by “Chenlun,” owner of a popular phishing kit and service. At the time, Chenlun had just launched new phishing pages designed to mimic postal services in the United States and at least a dozen other countries.
Phishing kits aren’t new, but Merrill said Chinese attack groups have recently introduced new delivery methods, seamlessly integrating their spam messages with Apple’s. iMessage technology, and RCS, the same “rich text” capabilities built into it Android devices.
“While smishing kits used to rely heavily on SMS for delivery, these days actors are using iMessage and RCS more because phone operators can’t filter them and they may have a higher success rate with these delivery channels,” he said.
It is not known exactly how the hackers chose their targets, or where their data can be obtained. A notice from MassDOT warns that “targeted phone numbers appear to be randomly selected and are not associated with an account or use of toll roads.”
Indeed, a reader shared on Mastodon yesterday that they found one of these SMS phishing attacks fooling a local toll operator, when they don’t even own a car.
Targeted or not, these phishing websites are dangerous because they are dynamically manipulated in real time by criminals. If you get one of these messages, just ignore or delete it, but please don’t visit the phishing site. The FBI asks that before you close the error, consider filing a complaint with the agency’s Internet Crime Complaint Center (IC3), including the phone number where the text appeared, and the website listed in the text.
Source link