The wise malware scheme for the first time, was noticed in the intended attacks last year we were gone now. In this scam, called “Click“A visitor to a crashed or cruel building we are asked to separate ourselves with bots by pressing a combination of keyboard buttons causing Microsoft Windows Downloading malware steals the password.
Clickfix attacks imitating the “Make sure you are testing by the” many websites used to divide real visitors from bots content. This particular scam is often starting with spam we look like that:
This attack Malware makes the CAPTCHA intended to distinguish people from bots.
Clicking the “I’m not robot” produces the Pop-up message asking the user to take three consecutive steps to prove their personality.

Making this color series stimulates the window to download malware stealing the password.
Step 1 Includes the keyboard key at the same time Windows and letter “r,” Run the windows “Run” will do any specified program in the system.
Step 2 Please press the “CTRL” key and the book “v” at the same time, attaching malicious code from the site’s necklace.
Step 3 – Pressing the “ENTER” key – causes windows to download and can introduce the malicious code with “Mshta.exe“Windows program is designed to run Microsoft HTML application files.
“The campaign brings many women’s malware, including XWorm, Lumma, Veynrat, Asyncrat, Danabot, and Netsupport Rat,” Microsoft Wrote at a blog post on Thursday. “According to some payload, a specific code presented with MSHTA.exe varies. Some of the PowerShippell power, JavaScript, the content contrary to (PE).
According to Microsoft, travel workers are identified to download malware with genuaries with cybercriminals Booking.com. The company said that the attackers have been sending malicious emails with Book.com, often looks at the review of negative tourists, requests from tourists, or internet proprieving – all in the BID to indicate an attacker.
On November 2024, Krebonsecurity reported that hundreds of hotels that use booking at some of that go work, and allow thieves to get control of Booking.com accounts. From there, they send critical reporting messages asking for financial information from newly-reserved backgrounds traveling through company app.
At the beginning of this month, security company Arctic Wolf Warning through the cruster of the clickfix addressed by the people working in the Health Care. The company said that those malicious code was decorated at the use of a professional HEP2GO redirection visitors in the Clickfish Prompt.
Alert (PDF) issued in October 2024 by Department of Health and US Services He warned that the clickfix can take a lot of ways, including fraud Google Chrome mistaken pages and full popups Facebook.
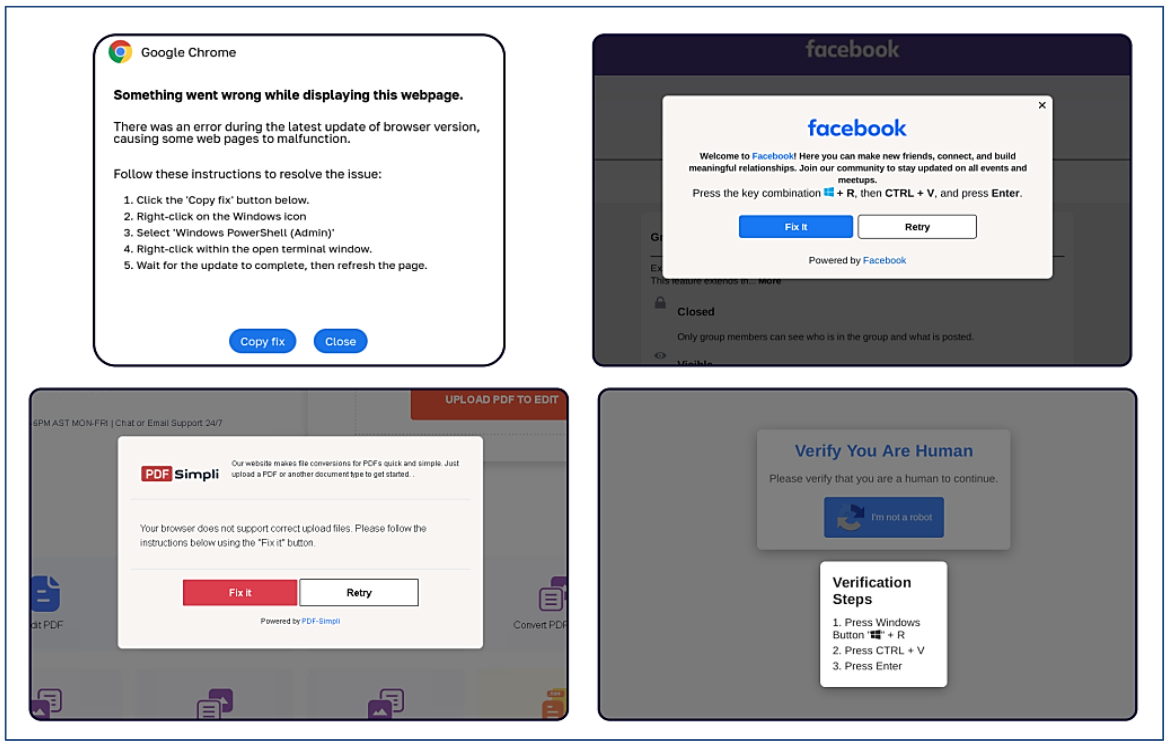
Clickfix Tact Tact Used Syonymen Websites make you Google Chrome, Facebook, PDFSimpli, and reckapcha. Source: Sekoia.
ClickFix attacks – and its dependence on her.exe – reminds the criminal techniques that are employed for hidden years in Emicrosoft office macros. Maclos Normal Malare that Microsoft is forced to start blocking the macros automatically in office documents that try to download content from the web.
Woes, security seller by email Evidence Has written a lot of clickfix attacks with a sensitive information emails including HTML attachments full of Microsoft Office. When it is opened, the attachment shows a Microsoft Word Picture by Pop-up error users to click on the “Solution” button or “How to Unoporrect” button.
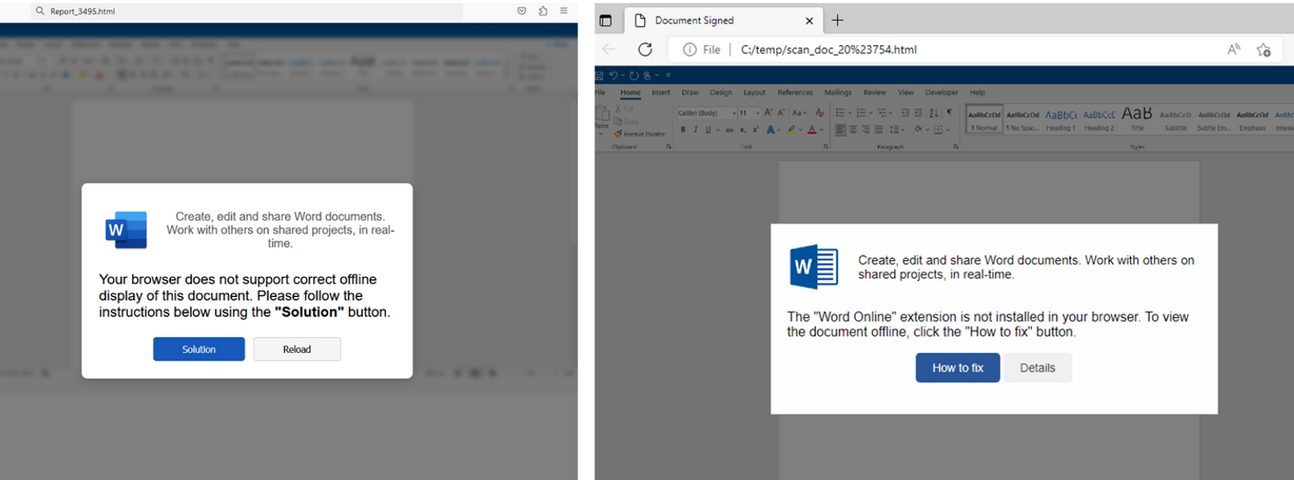
HTML files contain ClickFix commands. Examples of the attached attachment “Report_ (left) and” scan_doc_ “(right). Picture: Proof.
Organizations that wish to do so can take advantage of the Microsoft Group Policy restricts to protect windows to make the “Run” command when users hit Windows key and “R” at the same time.
Source link