The payment card giant MasterCard recently fixed an apparent bug in its domain name server settings that would have allowed anyone to intercept or divert the company’s Internet traffic by registering an unused domain name. The mismanagement continued for about five years until a security researcher spent $300 to register the domain and prevent it from being hijacked by cybercriminals.
A DNS lookup for the az.mastercard.com domain on Jan. 14, 2025 shows a misspelled domain name a22-65.akam.ne.
From June 30, 2020 until January 14, 2025, one of the key Internet servers that MasterCard uses to direct traffic to parts of the mastercard.com network was misnamed. MasterCard.com relies on five shared Domain Name System (DNS) servers from an Internet infrastructure provider Akamai [DNS acts as a kind of Internet phone book, by translating website names to numeric Internet addresses that are easier for computers to manage].
All Akamai DNS server names used by MasterCard must end in “akam.net” but one of them is not properly configured to trust the domain “akam.ne.”
This small but potentially serious typo was discovered recently by Philippe Catureglifounder of security agency Seralys. Caturegli said he guessed that no one has registered the akam.ne domain, which is under the authority of the chief domain officer of the West African country Niger.
Caturegli said it took $300 and a three-month wait to secure a domain by registering in Niger. After enabling the DNS server at akam.ne, he saw hundreds of thousands of DNS requests hitting his server each day from locations around the globe. Apparently, MasterCard wasn’t the only organization that had greased the DNS with greasy fingers to include “akam.ne,” but it was a big one.
If he had enabled the email server on his new akam.ne domain, Caturegli would likely have received stray emails directed to mastercard.com or other affected domains. If he abused his access, he could probably obtain the website’s encryption certificates (SSL/TLS certificates) that are authorized to receive and transmit web traffic to the affected websites. You may have been able to quietly obtain Microsoft Windows certificates from employees’ computers at the affected companies.
But the researcher said that he did not try to do that. Instead, he warned MasterCard that the site was theirs if they wanted it, copying the author from his notices. Hours later, MasterCard acknowledged the error, but said there was never a real threat to the security of its operations.
“We are looking into this issue and there is no risk to our systems,” a MasterCard spokesperson wrote. “This typo has now been corrected.”
Meanwhile, Caturegli received a request sent by Lots of insectsa program that offers financial rewards and recognition to security researchers who find bugs and work privately with the affected vendor to fix them. The message suggested his public disclosure of the MasterCard DNS error in a post on LinkedIn (after he had found the akam.ne domain) was not related to ethical security practices, and forwarded a request from MasterCard to have the post removed.
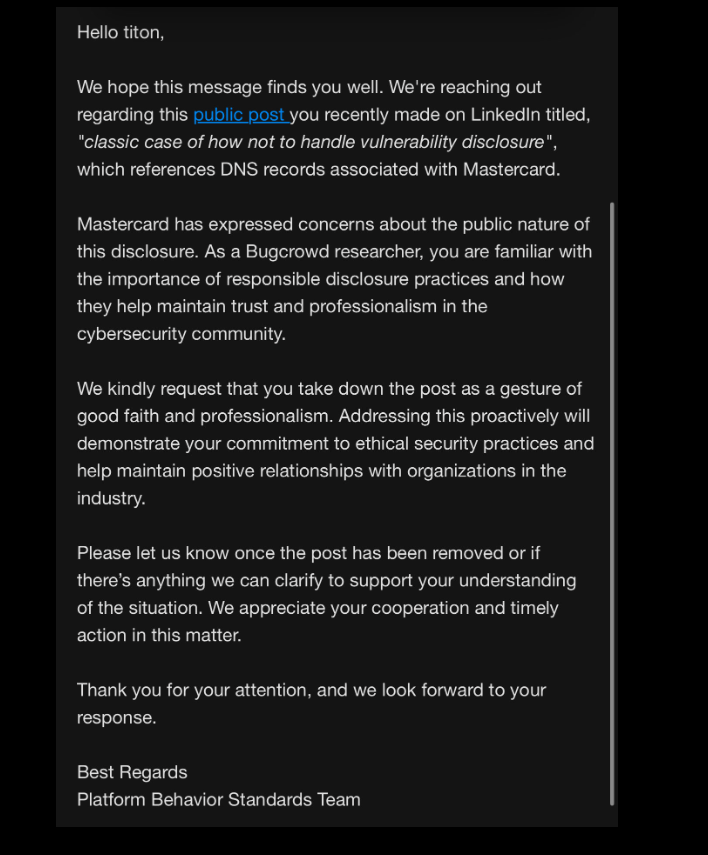
MasterCard application to Caturegli, aka “Titon” on infosec.exchange.
Caturegli said that although he has an account with Bugcrowd, he has never sent anything through the Bugcrowd program, and reported the issue directly to MasterCard.
“I did not disclose this matter to Bugcrowd,” Caturegli wrote in response. “Before making any public disclosures, I ensured that the affected domain was registered to prevent exploitation, to minimize any risk to MasterCard or its customers. This action, which we have taken at our expense, demonstrates our commitment to ethical safety practices and responsible disclosure.”
Most organizations have at least two authoritative domain name servers, but some handle so many DNS requests that they need to spread the load over additional DNS server domains. In the case of MasterCard, that number is five, so it stands to reason that if an attacker were able to gain control of one of those domains they would only be able to see about one-fifth of all incoming DNS requests.
But Caturegli said the reality is that most Internet users rely at least to some extent on public traffic forwarders or DNS resolvers such as Cloudflare again Google.
“So all we need is for one of these solvers to query our word server and store the result,” Caturegli said. By setting their DNS server records with a long TTL or “Time to Live” — a setting that can adjust the lifetime of data packets on the network — an attacker’s poisoned directives for the target domain can be broadcast by major cloud providers.
“With a long TTL, we might reroute a LOT more than 1/5 of the traffic,” he said.
The researcher said he hoped the credit card giant would thank him, or at least offer to cover the cost of purchasing the domain.
“We obviously disagree with this assessment,” Caturegli wrote in the following LinkedIn post about MasterCard’s public statement. “But we’ll let you be the judge – here are some DNS lookups we recorded before reporting this story.”
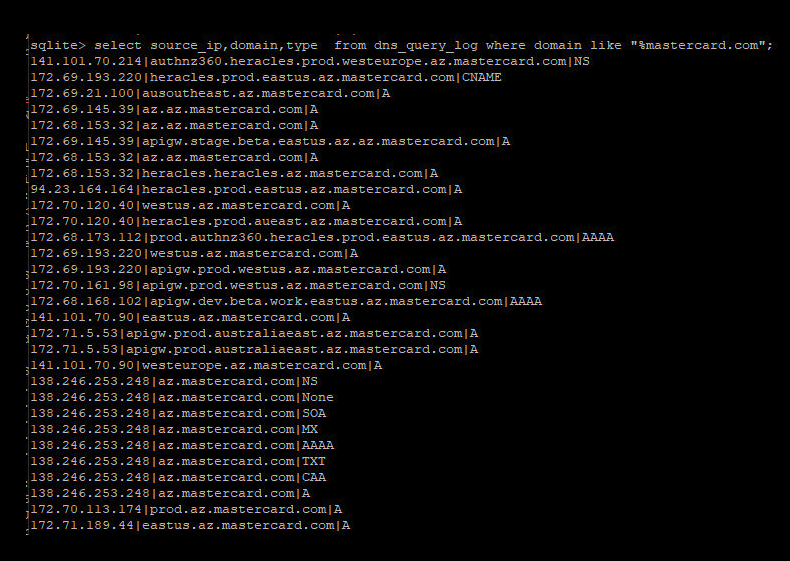
Caturegli posted this screenshot of potentially vulnerable MasterCard domains from a poorly configured domain.
As the screenshot above shows, the wrong DNS server was found involving the MasterCard subdomain. az.mastercard.com. It is unclear exactly how this subdomain is used by MasterCard, however their naming conventions suggest that the domains correspond to Microsoft’s production servers. Azure cloud service. Caturegli said all domains resolve to Internet addresses at Microsoft.
“Don’t be like Mastercard,” concluded Caturegli in his LinkedIn post. “Don’t dismiss the risk, and don’t let your marketing team handle security disclosures.”
One last note: The domain akam.ne was registered earlier — in December 2016 by someone using the email address [email protected]. Russian search giant Yandex reports that the user account belongs to “Ivan I.” from Moscow. Passive DNS records from DomainTools.com show that between 2016 and 2018 the domain was connected to an internet server in Germany, and that the domain was left to expire in 2018.
This is interesting given a comment on Caturegli’s LinkedIn post from a former Cloudflare employee who linked to a report he co-authored on a similar typing domain apparently registered in 2017 to organizations that may have mistyped their AWS DNS server as “awsdns-06.ne” instead of “awsdns-06.net.” DomainTools reports that this domain was also registered to a Yandex user ([email protected]), and was hosted by the same German ISP – Internet Team (AS61969).
Source link