SMS Kits Kits Responsors Kits Kits enjoy the amazing success that turns a phoxed photoged paying card data from the mobile wallets from apple including Google. Until recently, so-called “Sky“Very low-operative operators and shipping companies. But experts say the groups are now aimed at customers of international financial institutions, while enhancing the Cybercrime infrastructure and support staff.
A photo of the mobile device for the shared iPhone is one of the dynamic members. Image: previously
If you own mobile phones, the chances are the best two years ago have found at least instant message you warned for a roadbell, or patching package from US post service (USPS). Those who clicked the toolbar is brought to the website passing USPS or local road operator and requested payment card details.
The location will be space that the guest bank requires “verification” transactions by sending a single-time code for SMS. In fact, the bank sends that code mobile number to their customer’s file because fraudsters have just tried to sign up for the victim’s card information in the mobile bag.
If the visitor provides that one-time code, their payment card is added to the new Apple bag on the Apple device or the Google device controlled by the head. Criminals foretell writing multiple-stolen wallets or one apple, and sell those phone calls to the Scamers who use e-commerce and Tap-to-Pay transactions.
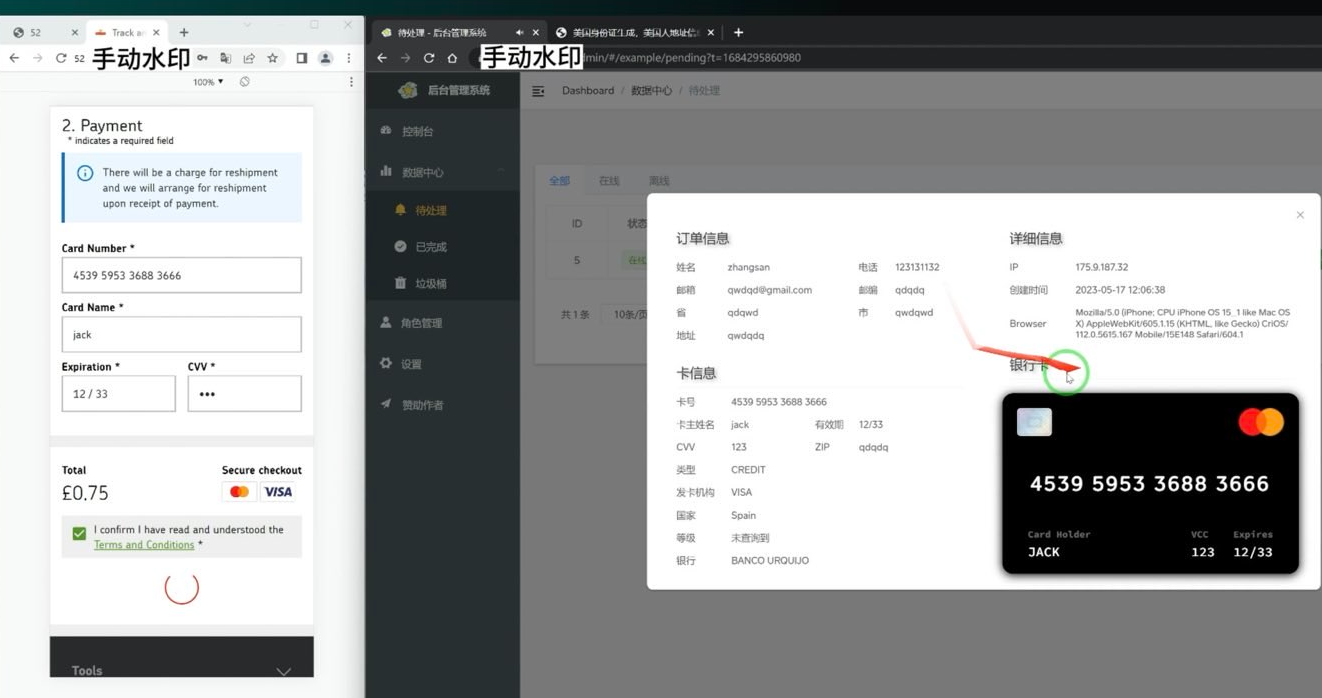
A screenshot of the administration panel of the beating kit. On the left is the data (test) data installed in the form of a critical details. The right we can see the Phishing kit has a card number provided in the payment card image. When phishing kit scan a card photo made of Apple or Google Pay, it causes an attacker bank to send a single-time code. Image: Ford Merrill.
Mikoiker “beating tread” appears PaintingThe first interception reports on August 2023 in the two-diversity of the various criminal groups in Chinese manifestations that appear to share certain infrastructure and new crime strategies. But it is not a little misnomer because the breeding crime breeding these groups are not SMS or text messages.
Rather, they are sent by website above apple Device users, and RCS on Google Android devices. Therefore, arrows exceed the full mobile phone networks and enjoy closer to 100 percent (at least until Apple and Google stops spammy accounts.
In a report published on March 24, the Switzerland Socker Intelligence Firm Product with a quick speeds of awakening from the heat from the beating, which views as a free workshop-operated group of the Chinese activities Daura, Lighthouseno Xinxin group.
The draining said they saw a major change in the underground economy, especially among the Chinese-speaking players in drugs compared to their Russian-speaking partners.
“Chinese-speaking characters presented new systems and free of costs, they are able to direct the basics of large users with complex services,” written information. “Their way marks the new era in underground business practices, emphasizing the stability and efficiency of cybercriminal operations.”
A new report from researchers in security firm Silent House Finds dynamic mimitating members expand for selling piching kits to the global financial institutions such as Kiss, Mastercard, Wages, Linebeside Accessand banks in Canada, Latin America, Australia and a comprehensive Asian-Pacific region.

Generosity generosity from a soft paypal heat. Image: silentpush.
Silentpush discovered that Smeshing Trad now is full of known types of international universe and the number of postalities, including communications, transportation, financial, financial, financial, financial, financial, financial, financial, financial, financial, financial, financial, financial, financial, financial, financial, financial, financial, financial, financial, finance.
According to a protected vehicle, the backgrounds used by the beating tread is rotated often, with approximately 25,000 tools for the abuse of the critical details at any time 8 days and the majority of Chinese catching companies: Army (AS132203) and Alaba (AS45102).
“For about two parts of all countries in the land aimed at [the] Triad skiing, is safe to say that it is actually addressed in all countries in modern infrastructure, North Korea, “and Russia,” nothing can say any enough to show Russia. Interestingly, although these are the hosted Chinese players, we have seen targeted conditions aimed at Macau and Hong Kong, both special Chinese administrative areas. “
Motivation Zach Edward He said his party received a risk that disclosed data at one of the books of the Sumwang Tribishing Praad, producing visits the visit to all of the hijackers operated. Based on that data, it is estimated that the older pages are the worn pages found more than a million visit 20 days.
The report notes that the Sliers Triads are “formerly involved in the former desk workers.
Moving Moming Members keep their Chinese trading channels in the Telegraph, regularly provide videos and photos of their workers hard work. Some of those pictures include large telephone walls used to send serious messages, as well as the personnel workers right in front of them to find any one-time codes.
As noted in February case how Showed data turns to apples and Google Wallets, one of those cash-output systems include the Android app including Android app including Android app including Android app including Android application. Iz NFCPotential NFC transactions from one of these digital wallets postponed in anywhere in the world. With a $ 500 monthly subscription
https: /www.youtube.com/watch? v = KqzjppppPaxB4c
The Chinese nations have just tried to use the NFC apps to buy Singapore Electores. And in the United States, California and Tennessee authorities arrested Chinese nations through the NFC apps in sales marketing cards.
Prodaft investigators said they were able to obtain a Panese Panese Party Participants who were registered for LucidA-service collision function were tied to the Xinxin group. The panel installed the victim figures that suggest crash campaigns keep a limited amount of 5 percent, while other backgrounds receive more than 500 hours a week.
“In one point in view, one website of the prince’s crime website capture 30 credit card records from a 550 victim of the victim of 750 days,” written.
The details of the Prodish Triad’s information has found such success in submitting their spam messages. For example, a certain amount of criminal details seems to send messages using a lot of Android device running like a single machine.
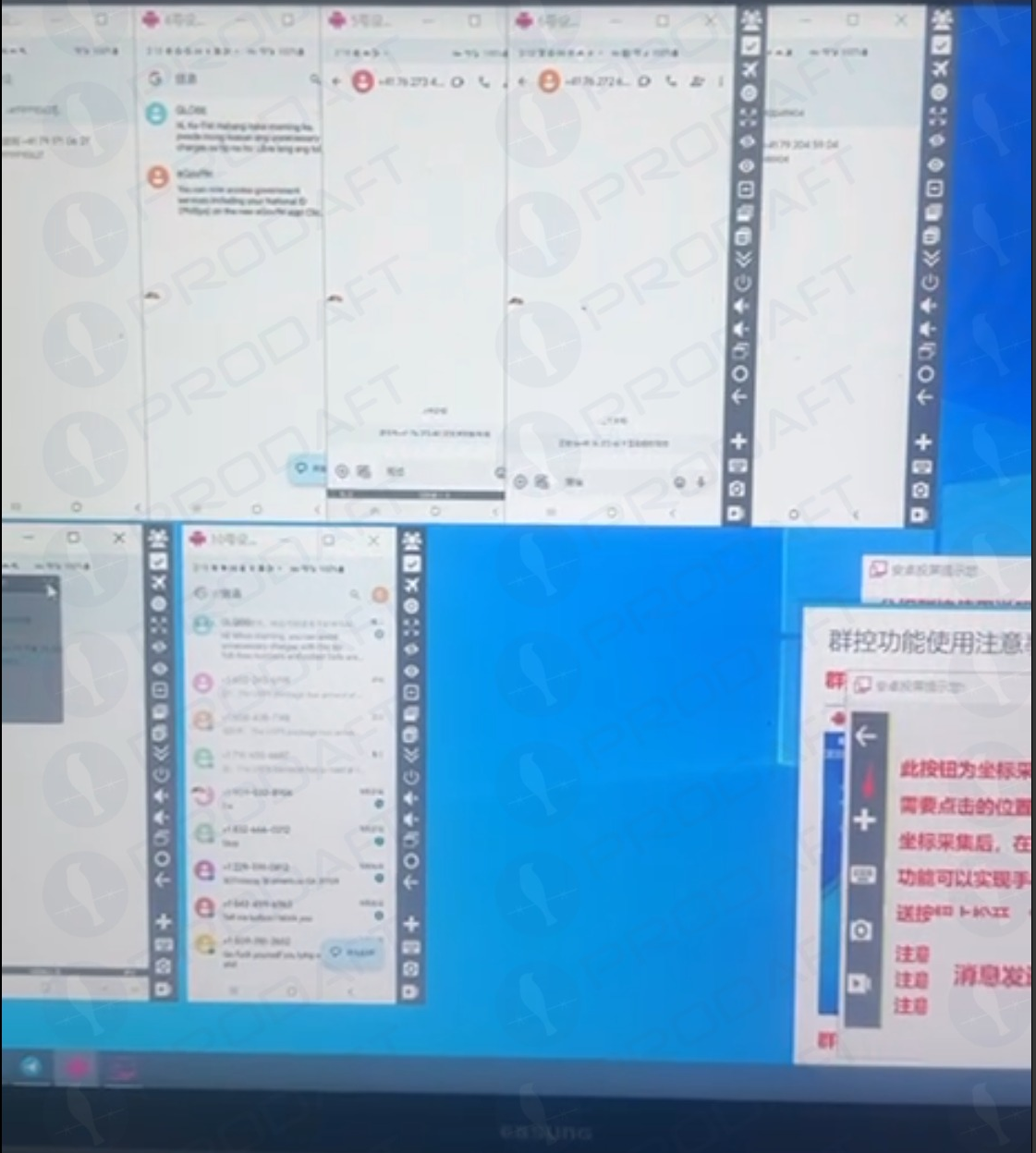
Phishers use multiple Android devices that plan to distribute and distribute RCS-based Campaigns. Image: previously
According to Prodort, the threatening players get phone numbers first in various ways including data, open source, or list purchased in underground markets. They exploited the spaces of technology in the Meter ID guarantee within both of the message platforms.
“IMESSAGE, this includes creating temporary apples with words that display uninheaded, while RCS abuse is made with the installation of the SENDER validation,” writes. “The delivery of the message occurs with default platforms using VoIP numbers or unlicensions, often submitted to multi-time campaigns that increase efficiency.
In addition, the links to the sensitive information included in these messages use the limited one-time URLs that expire or redirected based on the number of fingers in order to achieve security analysis, finding.
“The economy likes the attackers, not RC messages or IMesses receiving the cost of each message such as traditional SMS, enabling higher campaigns at applicable costs,” Prodimid continued. “The fullness of templates, target lakes, and tricks between these platforms emphasize the united threat, their strategies to install the world in a worldwide.”
Ford Merrill It works in the Socalianyance security study, CSIS Security Company. Merrill said at least one video of the window rides visible Chrome and can be used to load phone numbers and Blast numbers with RCS, iMessage, Amazon, Facebook, and WhatsApp.
“We’ve seen evidence suggests the power of one device to send about 100 messages per second,” said Melrill. “We also believe there is a power to find certain SIM cards for SIM EU SIM EUS SIM cards that allow you to register different SIM cards, and make those SIM cards on phone number or SIM’s existence on the mobile network.”
Experts say that the rapidly growing card wave persists because the most financial institutions that still fail to send one time codes with SMS certification card registration in apples or Google. AkrebonseConseCuring interviewees with a number of funds at the non-US financial institutions that spoke about the situation because they were not authorized to talk to the media. Those banks have completed one SMS time codes and now need customers to sign in to the mobile app before connecting their card to digital.
Source link