A group based in Russia called “Fin7,” known for phishing and malware attacks that have cost victim organizations an estimated $3 billion since 2013, was declared dead last year by US authorities. But experts say Fin7 has revived in 2024 – setting up thousands of websites imitating a range of media and technology companies – with the help of Stark Industries Solutionsa widespread hosting provider that is a constant source of cyber attacks against Russia’s enemies.
In May 2023, the US attorney for the state of Washington announced that “Fin7 is no longer an organization,” after prosecutors obtained convictions and prison sentences for three men found to be hackers or high-level executives of Fin7. This was a bold announcement against a group that the US Department of Justice described as a criminal enterprise with more than 70 people organized into different business units and groups.
The first signs of a Fin7 revival came in April 2024, where Blackberry wrote about breaking into a major auto company that started with malware that used a typosquatting attack aimed at people looking for a popular free network scanning tool.
Now, researchers at the security company Shut up Pusha they say they have developed a way to map Fin7’s rapidly growing cybercrime infrastructure, which includes more than 4,000 hosts that use a variety of exploits, from typosquatting and blocked ads to malicious browser extensions and spear-phishing sites.
Silent Push said it found Fin7 targeting or spoofing domains including American Express, Affinity Power, Airtable, The Alliant, Android developer, Asana, Bitwarden, Bloomberg, Cisco (Webex), CNN, Costco, Dropbox, Grammarly, google, Goto.com, Harvard, Lexis Nexis, Meta, Microsoft 365, It’s an intermediate journey, Netflix, Paycor, Quickbooks, Hurry up, Reuters, Regions Bank Onepass, RuPay, SAP (Ariba), Trezor, Twitter/X, The Wall Street Journal, Westlawagain Zoom inamong others.
Zach Edwardsa senior threat analyst at Silent Push, said many Fin7 domains are innocuous websites for ordinary businesses that sometimes include text from default website templates (the content on these sites is usually unrelated to the stated business or business purpose).
Edwards said Fin7 does this to “age” the domains and give them a good or at least a bad reputation before they are eventually converted for use in hosting specific phishing pages.
“It took them six to nine months to ramp up, but since January of this year they’ve been humming along, building phishing infrastructure and aging domains,” Edwards said of the cybercrime group.
In typosquatting attacks, Fin7 registers domains similar to those of popular free software tools. Those look-alike domains are then advertised on Google so that their sponsored links appear prominently in search results, often above the official source of the software in question.
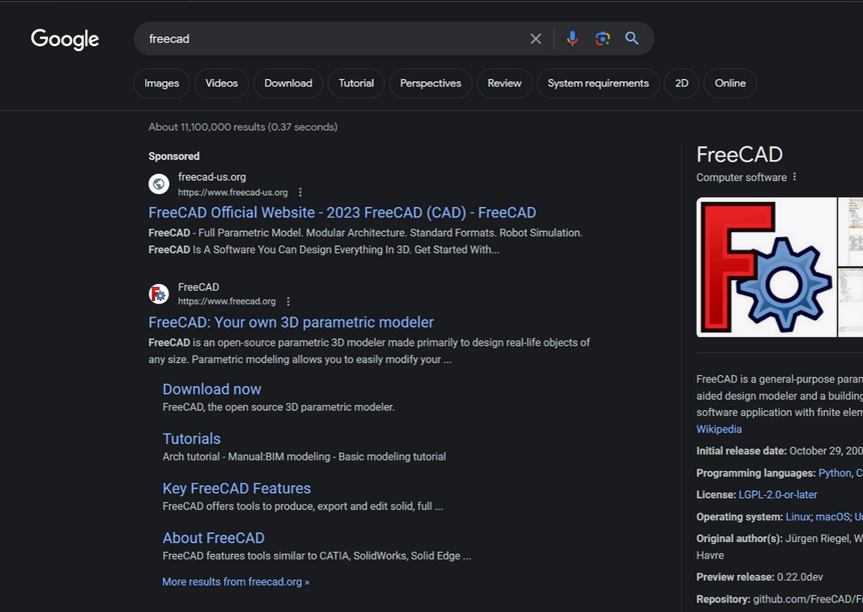
The malicious site FreeCAD appeared as a sponsored result in Google search results earlier this year.
According to Silent Push, software currently targeted by Fin7 includes 7-zip, PuTTY, ProtectedPDFViewer, AIMP, Notepad++, Advanced IP Scanner, AnyDesk, pgAdmin, AutoDesk, Bitwarden, Rest agent, Python, Higher Textagain Node.js.
In May 2024, the security company in Sentire warned that Fin7 has been spotted using Google sponsored ads to serve up hackers who encourage people to download deceptive browser extensions that install malware. Malwarebytes blogged about the same campaign in April, but it didn’t reveal the work from either group.
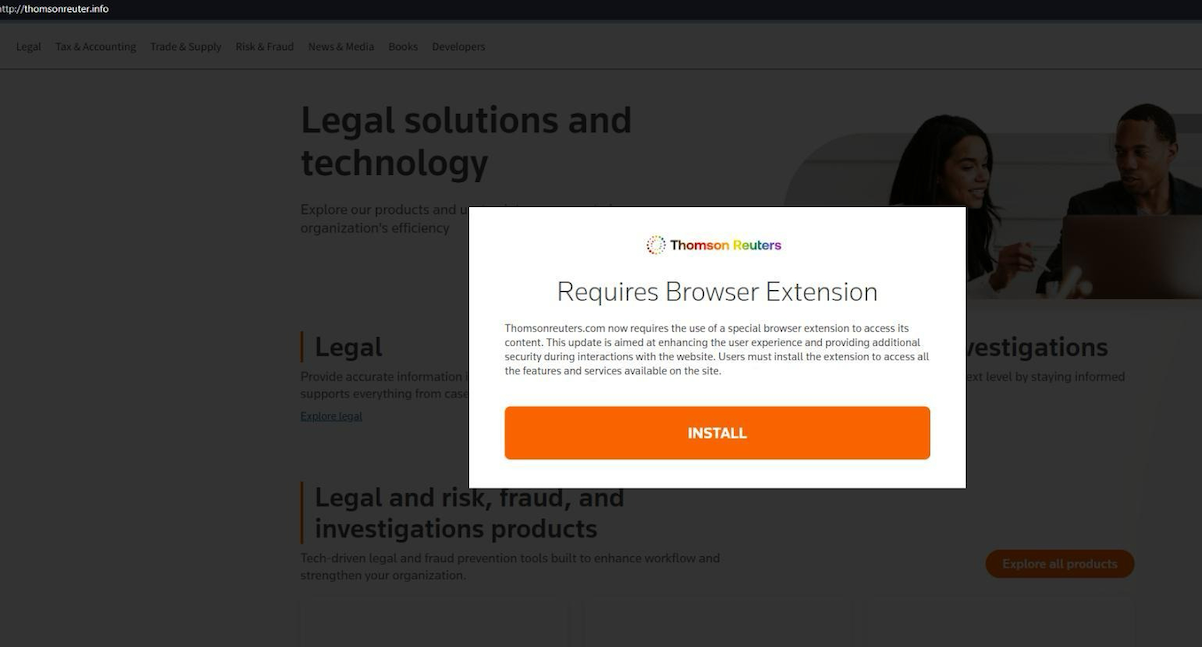
A pop-up on the Thomson Reuters typing site that tells visitors they need to install a browser extension to view news content.
Edwards said that Silent Push had acquired new Fin7 domains after the trial of an organization that had been targeted by Fin7 years ago and suspected that the group had become active again. A search for hosts that match the known profile of Fin7 reveals one active site. But Edwards said one site points to several other Fin7 properties at Stark Industries Solutions, a major hosting provider that appeared just two weeks before Russia invaded Ukraine.
As KrebsOnSecurity wrote in May, Stark Industries Solutions is being used as a watchdog for wave after wave of cyberattacks against Ukraine tied to Russian military and intelligence agencies.
“FIN7 leases a significant amount of IP dedicated to Stark Industries,” Edwards said. “Our analysts found many Stark Industries IPs dedicated solely to hosting the FIN7 infrastructure.”
Fin7 once famously worked behind fake cybersecurity companies – with names like these Combi Security again Bastion Secure – which they use to hire security experts to help with ransomware attacks. One of the new Fin7 domains identified by Silent Push is cybercloudsec[.]compromising to “grow your business with our IT, cybersecurity and cloud solutions.”
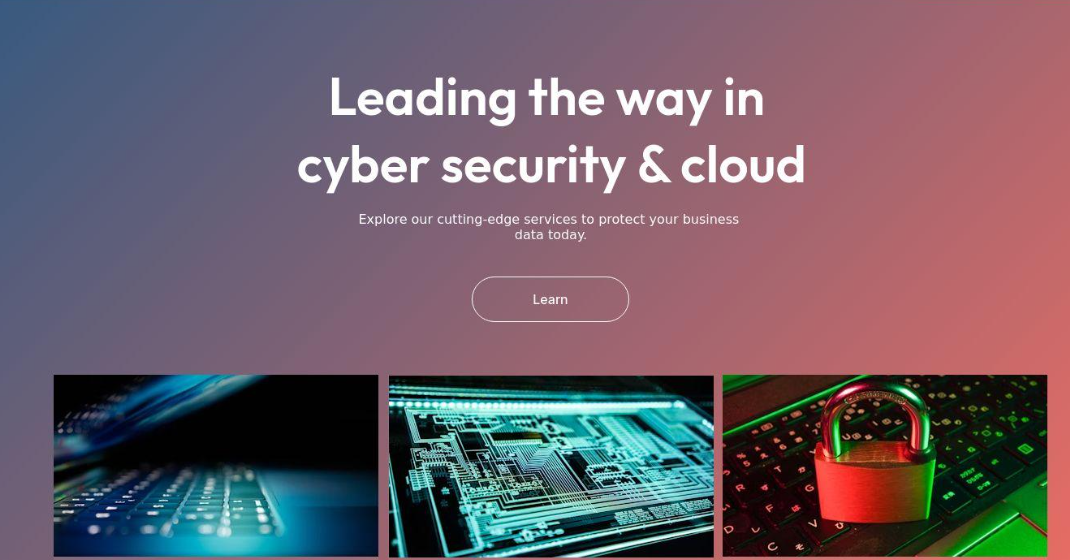
Fake Fin7 security company Cybercloudsec.
Like other phishing groups, Fin7 hosts current events, and is currently targeting tourists traveling to France for the Summer Olympics later this month. Among the new Fin7 domains found in Silent Push are several sites that hack people looking for Louvre tickets.
“We believe this study makes it clear that Fin7 is back and growing fast,” Edwards said. “We hope that law enforcement will take note of this and put Fin7 back on their radar for further enforcement action, and that a few of our competitors will be able to take this pool and expand to all or a good portion of it. infrastructure.”
Further reading:
Stark Industries Solutions: Iron Hammer in the Cloud.
A 2022 dive into Fin7 from Swiss intelligence firm Prodaft (PDF).
Source link