A Chinese company in charge of providing domain names ending in “.up” has been given until mid-August 2024 to demonstrate that it has installed systems to handle phishing reports and stop abusive domains, or else lose its license to sell domains. The warning comes amid new findings that .top was the most common extension for phishing websites in the past year, second only to domains ending in “.com.”
Photo: Shutterstock.
On July 16, the Internet Corporation for Assigned Names and Numbers (ICANN) sent a letter to the owners of the .top domain registration. ICANN has filed hundreds of enforcement actions against domain registrars over the years, but this is believed to be the first time that ICANN has singled out a domain registrar responsible for maintaining an entire top-level domain (TLD).
Among other reasons, the wrongful accused the registry of failing to respond to reports about phishing attacks involving .top domains.
“Based on information and records collected over several weeks, it was determined that .TOP Registry does not have a process to promptly, thoroughly, and reasonably investigate and act on reports of DNS Abuse,” the ICANN letter reads (PDF) .
ICANN’s warning redacted the recipient’s name, but records show the .top registry is being used by a Chinese entity called. Jiangsu Bangning Science & Technology Co. Ltd. Company representatives have not responded to requests for comment.
Domains ending in .top are prominently represented in a new phishing report released today by Interisle Consulting Groupwhich receives phishing data from several sources, including Anti-Phishing Task Force (APWG), OpenPhish, PhishTankagain Spamhaus.
Interisle’s latest study examined nearly two million phishing attacks last year, and found that phishing sites accounted for more than four percent of all new .top domains between May 2023 and April 2024. Interisle said .top has approximately 2.76 million domains in its stable. , and that more than 117,000 of those were phishing sites in the past year.
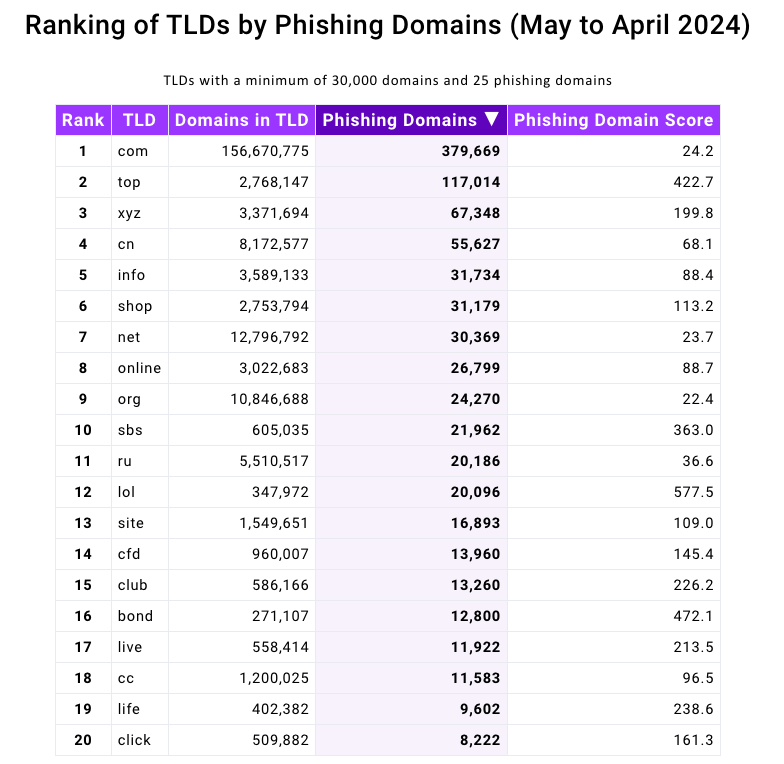
Source: Interisle Consulting Group.
ICANN said its review is based on information it has gathered and learned about .top domains over the past few weeks. But the fact that a high number of phishing sites are registered through Jiangsu Bangning Science & Technology Co Ltd. it is not a new thing.
For example, more than 10 years ago the same Chinese registry was the fourth most common source of phishing websites, as tracked by APWG. Note that the APWG report cited below was published more than a year before Jiangsu Bangning received ICANN approval to launch and manage the new .top registry.
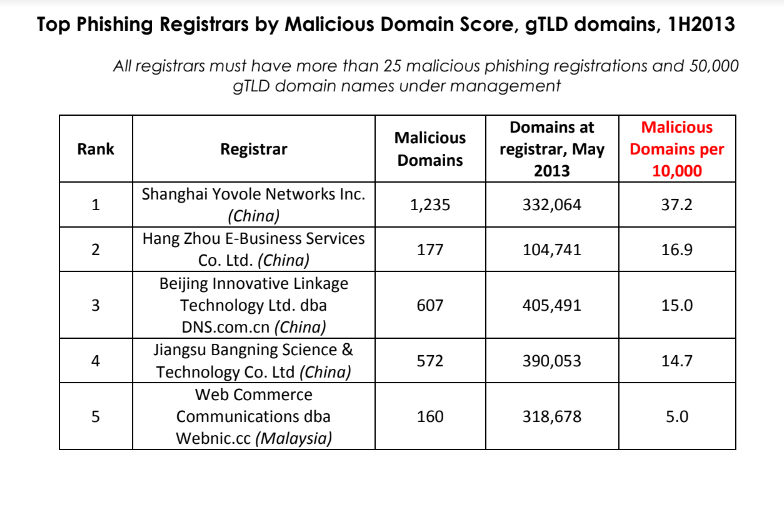
Source: APWG’s 2013 phishing report, two years before .top existed.
An interesting new ally in the phishing space is the growth of phishing pages hosted using the InterPlanetary File System (IPFS), an extended data storage and delivery network based on a peer-to-peer network. According to Interisle, the use of IPFS to host and launch phishing attacks – which can make phishing sites more difficult to take down – has increased by a staggering 1,300 percent, to nearly the same number of phishing sites reported last year.
A report last year from Interisle found that domain names ending in “.us” – the top-level domain for the United States – were among the most common in phishing scams. Although .us domains aren’t even on the Top 20 list of this year’s study, “.com” has maintained its perennial #1 spot as the largest source of phishing domains overall.
Last year, the phishiest domain registrar to date was Freenom, a now-defunct registrar that offered free domains in several country code TLDs, including .tk, .ml, .ga and .cf. Freenom went out of business after being sued by Meta, alleging that Freenom was ignoring abuse complaints while monetizing traffic from abusive sites.
After Freenom’s demise, hackers quickly moved to other cheap new TLDs and to services that allow free, anonymous domain registration – especially domain services. For example, Interisle has discovered phishing attacks involving websites created on Google blogspot.com last year it increased to 230%. Other subdomain services that have seen significant growth in phishing domains include weebly.com, github.io, wix.comagain Change the IPthe report notes.
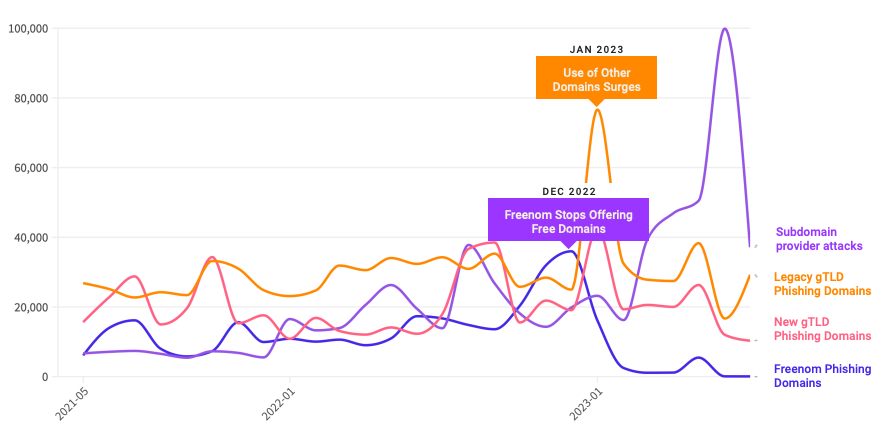
Source: Interisle Consulting.
Partner of Interisle Consulting Dave Piscitello said ICANN could easily send similar warning letters to other high-profile registries, noting that scammers and phishing scams often circle the same TLDs from time to time – including .xyz, .information, .support again .lolall of which saw a lot of business from hackers after Freenom’s lies.
Piscitello said domain registrars and registries can significantly reduce the number of phishing sites registered through their services by flagging customers who try to register large volumes of domains at once. Their research found that at least 27% of domains used for phishing were mass-registered – meaning the same registrant paid for hundreds or thousands of domains in quick succession.
The report includes a case study in which this year’s fraudster registered 17,562 domains over an eight-hour period – about 38 domains per minute – using .lol domains all made up of random letters.
ICANN tries to resolve contractual disputes privately with subscribers and the registrar’s community, and experts say the nonprofit often publishes enforcement letters if a recipient ignores its privacy notices. Indeed, the ICANN letter notes that Jiangsu Bangning did not even open its email notifications. It also cited the registry for falling behind on its ICANN membership fees.
With that in mind, a review of ICANN’s public compliance work suggests two trends: First is that there have been far fewer public compliance and enforcement actions in recent years – even as the number of new TLDs has increased dramatically.
The second is that in many cases, the failure of the registry or registrant to pay the annual ICANN membership fees is cited as the reason for the warning letter. A review of nearly a dozen enforcement letters ICANN has sent to domain registrars since 2022 shows that failure to pay fees was cited as a reason (or i reason) in violation at least 75 percent of the time.
Piscitello, a former ICANN board member, said nearly all infringement notices sent during his time at ICANN were because the registrar owed money.
“I think some of it is just lipstick to suggest that ICANN is above DNS Abuse,” Piscitello said.
KrebsOnSecurity has sought comment from ICANN and will update this story when they hear back.
Source link