More than a million domain names — including many registered by Fortune 100 firms and product protection companies — are at risk of being taken over by hackers because of authentication weaknesses at a large number of web hosting providers and domain registrars, a new study finds.
Photo: Shutterstock.
Your web browser is able to find a site like example.com thanks to the Global Domain Name System (DNS), which acts as a kind of Internet phone book by translating human-friendly website names (example.com) into the Internet of numbers. addresses.
When someone registers a domain name, the registrar will usually provide two sets of DNS records that the customer needs to assign to their domain. Those records are important because they allow web browsers to find the Internet address of the hosting provider running that domain.
But potential problems can arise when a domain’s DNS records are “disabled,” meaning that the authoritative name server does not have enough information about the domain and cannot resolve queries to locate it. A domain can be disabled in various ways, such as when an Internet address is not assigned, or because the name servers in the domain’s authoritative record are not configured correctly or are missing.
The reason disabled domains are a problem is that a number of Web hosting and DNS providers allow users to claim domain control. without accessing the true owner’s account from their DNS provider or registrar.
If this threat sounds familiar, that’s because it’s not new. Back in 2019, KrebsOnSecurity wrote about thieves using this method to seize control of thousands of domains registered to GoDaddy, and using those to send bomb threats and sextortion emails (GoDaddy says they fixed that vulnerability in their systems shortly after that 2019 story ).
In the 2019 campaign, spammers created accounts on GoDaddy and were able to take over compromised domains by registering a free account on GoDaddy and being assigned the same DNS servers as the hijacked domain.
Three years before that, a similar full vulnerability was described in a blog post by a security researcher Matthew Bryantwho showed how one can control at least 120,000 domains with DNS vulnerabilities from some of the world’s largest hosting providers.
Surprisingly, a new study released jointly today by security experts at Infoblox again The Eclypsium finds this authentication weakness still exists in a large number of hosting and DNS providers.
“It’s easy to use, very hard to see, and completely avoidable,” it said Dave Mitchell, principal threat researcher at Infoblox. “Free services make it easy [to exploit] on the scale. And most of these are several DNS providers. “
LIVING DUCKS
An Infoblox report found that there are many cybercriminal groups that abuse these hijacked domains as a “traffic distribution system” scattered around the world, which can be used to hide the true source or destination of web traffic and link Web users to malicious or fake websites.
Controlling domains in this way can also allow thieves to impersonate trusted products and abuse their good or at least neutral reputation when sending email from those domains, as we saw in 2019 with the GoDaddy attack.
“Hijacked domains have been directly used in phishing attacks and scams, as well as large-scale spamming programs,” reads the Infoblox report, which refers to the disabled domains as “Sitting Ducks.” “There is evidence that some sites were used for Cobalt Strike and other command and control (C2) malware. Some attacks have used stolen domains in phishing attacks by creating domains that look like others. Several actors have accumulated stolen domains for unknown purposes.”
Eclypsium researchers estimate that there are currently around one million Sitting Duck sites, and that at least 30,000 of them have been hijacked for malicious use as of 2019.
“As of the time of writing, most DNS providers allow this with weak or no verification of domain ownership for a given account,” wrote Eclypsium.
Security firms say they have found many of the domains vulnerable to Sitting Duck that were originally registered by product protection companies that specialize in defensive domain registration (keeping look-alike domains for top brands before those names are taken over by fraudsters) and fighting trademark infringement.
For example, Infoblox discovered cybercriminal groups using the domain name Sitting Duck clickermediacorp[.]comwhich was originally registered instead of CBS Interactive Inc. is a product protection company MarkMonitor.
Another hacked Sitting Duck site — anti-phishing[.]org – registered in 2003 by Anti-Phishing Task Force (APWG), a nonprofit cybersecurity organization that closely tracks phishing attacks.
In many cases, researchers found Sitting Duck domains that appeared to be configured to auto-renew at the registrar, but the authoritative DNS or hosting services were not renewed.
Researchers say Sitting Duck sites all have three qualities that make them vulnerable to being taken:
1) the domain uses or sends authorized DNS services to a different provider than the domain registrar;
2) the domain’s authoritative name servers have no information about the Internet address to which the domain should point;
3) an authorized DNS provider is “exploitable,” meaning an attacker can look up a domain from the provider and set DNS records without having access to a valid domain owner’s account at the domain registrar.
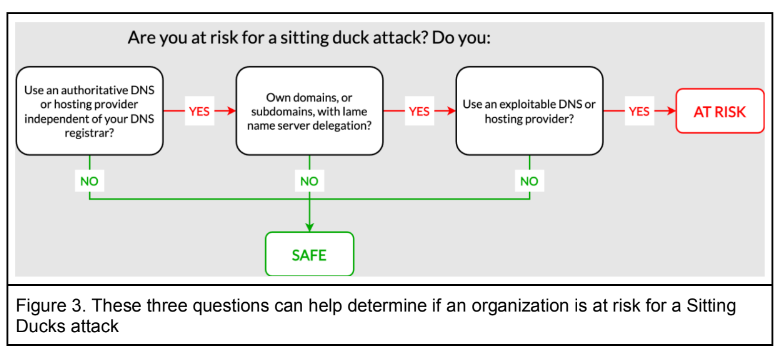
Photo: Infoblox.
How does one know if a DNS provider is usable? There is a regularly updated list published on it GitHub called “Can I take over DNS,” which has been documenting DNS provider exploitation for the past few years. The list includes examples of each DNS provider named.
In the case of the aforementioned Sitting Duck clickermediacorp domain[.]com, the domain was originally registered by MarkMonitor, but it appears to have been stolen by scammers by claiming it from a web hosting company. DNSMadeEasyowned by Digicertone of the industry’s largest issuers of digital certificates (SSL/TLS certificates).
In an interview with KrebsOnSecurity, DNSMadeEasy founder and senior vice president Steve Jobs he said the problem is not his company’s to solve, noting that DNS providers who are not domain registrars have no real way to verify that a given customer legitimately owns the desired domain.
“We close abusive accounts when we find them,” said Jobe. “But it is my belief that the burden must be limited [domain registrants] themselves. If you’re going to buy something and point it where you can’t control it, we’re not going to stop that.”
Infoblox, Eclypsium, and the DNS wiki list at Github all claim the web giant The Digital Ocean is among the hosting firms at risk. In response to questions, Digital Ocean said it is looking at options to reduce such activity.
“The DigitalOcean DNS service is not authorized, and we are not the domain registrar,” Digital Ocean wrote in an emailed response. “When a domain owner grants authority to our DNS infrastructure with their registrar, and they allow their ownership of that DNS record in our infrastructure to lapse, that becomes a ‘disabled delegate’ under this hijacking model. We believe that the root cause, ultimately, is mismanagement of the domain name configuration by the owner, such as leaving your keys in your car unlocked, but we appreciate the opportunity to adjust our monitoring protocols for unauthorized DNS service in an effort to help reduce the impact of sanity expiration on the authorized DNS level. We are in contact with research teams to explore additional mitigation options.”
In a statement provided by KrebsOnSecurity, the hosting provider and registrar Hostinger he said they are working on a solution to prevent attacks on disabled ducks “in the coming weeks.”
“We are working on implementing a SOA-based domain authentication system,” Hostinger wrote. “Custom nameservers with a record of Initial Authority (SOA) will be used to verify that the domain really belongs to the customer. We aim to launch this easy-to-use solution by the end of August. The last step is to revoke preview domains, a task sometimes used by clients with malicious intent. The preview domains will be retired at the end of September. Legitimate users will be able to use randomly generated subdomains instead.”
What DNS providers have struggled with this issue in the past to address these authentication challenges? Security firms say that in order to claim a domain name, best practice providers provide the account holder with random name servers that require a change to the registrar before the domains go live. They also found that best practice providers use a variety of methods to ensure that newly assigned name server hosts do not match previous server assignments.
[Side note: Infoblox observed that many of the hijacked domains were being hosted at Stark Industries Solutions, a sprawling hosting provider that appeared two weeks before Russia invaded Ukraine and has become the epicenter of countless cyberattacks against enemies of Russia].Both Infoblox and Eclypsium said that without more cooperation and less finger-pointing by all involved in global DNS, attacks on sitting duck domains will continue to rise, with domain registrants and ordinary Internet users caught in the middle.
“Government agencies, regulators, and standards bodies should consider long-term solutions to the vulnerability in the DNS management attack environment,” the Infoblox report concluded.
Source link